Industrial Cybersecurity and Edge Computing
By controlling data closer to its source and therefore deciding which data needs to be sent to the cloud, the cybersecurity risks of theft or improper access to information are much lower with Edge Computing.
The growth of Edge Computing in Industry
Edge computing adoption has witnessed a significant amount of growth in recent years. A recent report by Research and Marketsrl ecords that the global edge computing market size is anticipated to reach $155.90 billion by 2030.
The industrial sector is immersed in profound changes that are changing its usual dynamics. By digitizing equipment and processes, they are seeking to optimize time and costs and implement new business models that provide them with more value. Implementing these digitization processes involves collecting a large volume of data, analyzing it and understanding what decisions need to be made and what actions need to be taken.
The IT industry has been using the Cloud Computing model for years, a centralised model of data analysis, in large processing centres that are located in servers with great computing power but far away from the source of the data.
This model, however, poses a number of problems and arouses some misgivings in the industrial world. A new computing model is therefore emerging strongly in the industry: Edge Computing. This model consists of complementing cloud processing with data processing at the edge of the network, i.e at nodes much closer to where the data is captured.
Barbara IoT has recently conducted a study analysing the level of knowledge, needs and use cases around Edge Computing in industrial companies that we invite you to download if you want to know more details about the implementation of this technology in industry.
Edge computing is in full expansion: while in 2019 Grand View Research estimated the value of the edge computing market at $3.5 billion, IDC is already predicting that by 2022 the value of the edge computing market will rise to $40 billion, rising to $64 billion by 2025.
And one of the big reasons for this trend is that it brings 3 major advantages for the industrial sector compared to centralising computing in a single point (the cloud):

1. Scalability: by distributing the storage and processing of data across many locations, the growth of investment in infrastructure and capacity for higher traffic volumes or better algorithms is much more controlled.
2. Increased data security and sovereignty: by controlling data from its source location and therefore deciding what and when to send to the cloud, cybersecurity risks due to theft or improper access to information are reduced.
3. Greater efficiency: data analysis frequencies from the edge allow working with thousands of data almost instantaneously, and analysis and response times are in the order of milliseconds. This allows for almost real-time use cases, unthinkable in cloud environments more oriented towards offline analysis of batches of information.
Edge AI: bringing intelligence to the edge of the network
Another technology trend that analysts see gaining momentum in 2022 is aimed at developing use cases in the field of industrial digitisation through the data that can be collected at the edge. This is Artificial Intelligence (AI) applied at the edge, known as "Edge AI" .
Edge AI is a technology that consists of using Machine Learning algorithms to process data generated by devices (IoT sensors, industrial equipment, etc.) at a local level. This processing is carried out in Edge Nodes that are located and connected locally to the data sources themselves. Part of what has driven the growth of edge computing adoption in industries is actually, artificial intelligence.
Edge AI benefits from the advantages of Edge Computing and also provides a much more advanced computing model for data. With this technology, actions and decisions can be automated based on the data itself, further increasing the efficiency and effectiveness of industrial digitisation.
An example of the use of Edge AI technology in the industrial world, is the Predictive Maintenance. Thanks to the information obtained by sensors, industrial equipment and other IoT devices and through algorithms that analyse the data, look for patterns of behaviour and draw conclusions, it is possible to find out the probability of failure of a machine or element in, for example, a production line and thus decide when it is best to make a controlled stop to carry out maintenance work.
Cybersecurity at the Edge
Edge computing minimizes vulnerabilities linked to the transfer of data to the cloud (unlike cloud computing). The fact that the data is controlled from a local element, the edge node, significantly reduces this risk. However, this computing model also faces a number of cybersecurity risks that are important to be aware of when deploying on the Edge.
"Being a network architecture that relies on distributed, even unattended resources, connected in many cases to critical elements, its security, protection and monitoring design requires special attention. This is of much greater relevance when Edge Nodes can operate the very industrial equipment to which they are connected."
Good cyber-security practices applied to the Edge therefore mainly involve: 1) To ensure the protection of the edge nodes 2) to mplement a DevSecOps development strategy.
In addition, it would also be good to incorporate into the edge computing model some protection mechanisms that are already developed in cloud computing models: system integrity, information availability and secure data search.
Edge Nodes, the bridge between the network and industrial equipment
Edge nodes are responsible for both isolating industrial equipment from potential attacks from the network and protecting the data that industrial equipment captures and sends to the edge nodes themselves.
To this end, the edge nodes to be deployed must have protection mechanisms in place for this purpose, and they must also be remotely upgradeable.
Another good practice is to develop logic on the edge nodes that allows them to update not only themselves but also the industrial equipment to which they are connected.
DevSecOps: Cybersecurity as part of the development cycle
The DevOps methodology promulgates that development and systems teams, processes and tools should not be separated. The entire lifecycle of an application, from design to production deployment and maintenance, should be conceived as an integrated whole. In this way, it is the same engineers who code both the application and the tools to test and deploy it in an automated way in different environments.
The DevSecOps methodology consists of introducing cybersecurity into the above dynamics, so that it becomes part of the lifecycle of an application.
This methodology, applied to the development of Edge applications, helps to prevent cybersecurity risks that threaten Edge nodes and the equipment to which they connect.
Barbara The Cybersecure Edge Platforma
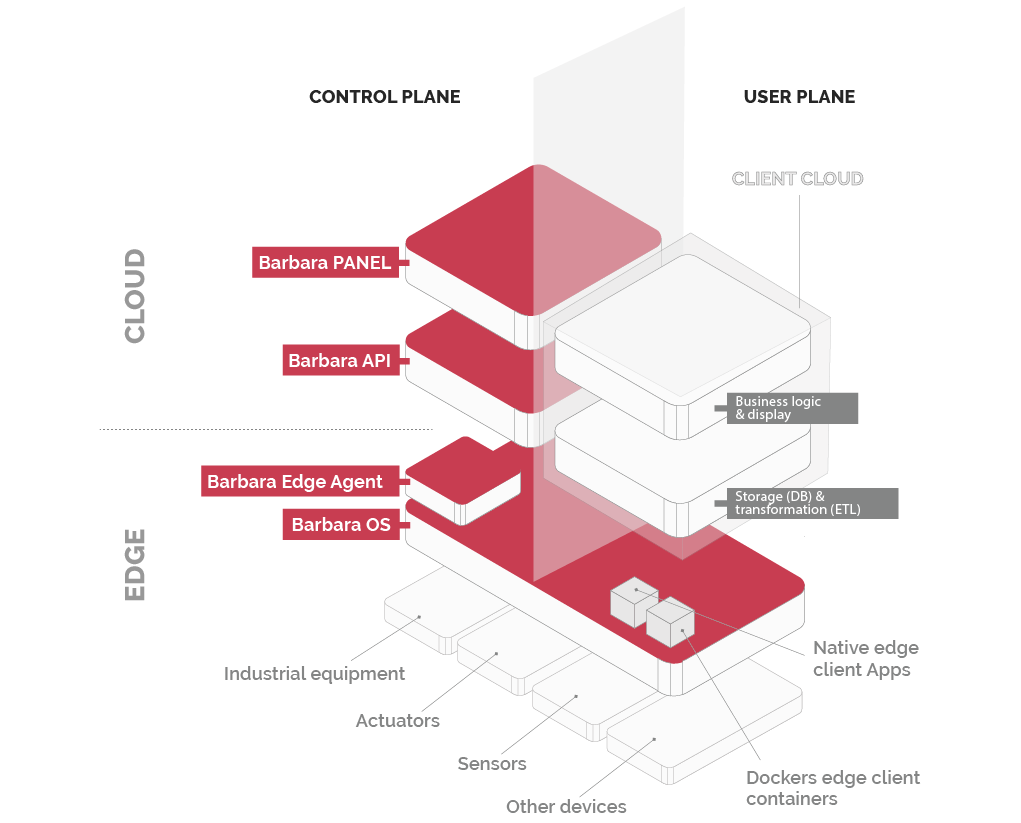
Barbara is the Cybersecure Industrial Edge Platform designed to govern distributed intelligence. It has been built with cybersecurity at its core is equipped with a set of functionalities that guarantee the privacy and resilience of the system.
In doing so, we have also followed key recommendations from organisations such as the GSMA, OWASP or the Industrial Internet Consortium (IIC) and industry standards such as IEC-62443.
Technologies that ensure the cybersecurity of the Barbara platform include:
- Provisioning and start-up system configured so that the initial configuration and communications certificates can be tailored to each company.
- Ensuring system integrity by executing cryptographic check algorithms during start-up, detecting possible anomalies.
- Hardware Secure Boot on hardware platforms with Trusted Platform Modules systems, so that binary file signatures are verified at boot time.
- Full encryption of all data at rest, preventing the extraction of sensitive data.
- Factory hardening of the device, removing default open network services and other vulnerable ways of accessing the device such as the user-password combination.
- User permissions management, segmenting access to data in anticipation of the risk of privilege escalation.
- Error management through tracing, detecting potentially security risky events.
- Monitoring and self-correction system, reducing the downtime of a device due to failure, and allowing autonomous and automatic correction of system problems.
- Certificate management through identity and access control based on cryptographic certificates, which are unique for each device. This is done transparently to the end user and is manageable remotely through the Remote Management Panel or directly through Barbara API.
If you want to know more about the Barbara platform, you can download our product sheet.








